Cybersecurity: Top 100 Influencers and Brands
Disclaimer: As ever with these lists, it must be stressed that the ranking below is by no means a definitive measurement of influence, as there is no such thing. The people listed below are undoubtedly influential when it comes to driving discussion within the context of cybersecurity.
The PageRank based methodology we use to extract infl uencers on a particular topic (tweets mentioning #cybersecurity or “cybersecurity” in this case) takes into account the number and quality of contextual references that a user receives. These calculations are independent of a user’s number of followers, but we do fi lter our lists based on how much a user is engaged in the conversation and the influence they drive through their networks.
Cybersecurity is becoming an ultimate priority for governments and businesses in 2015. Target, Sony, Pinterest and Adobe are among businesses that fell victim to hacking in the past 4 years.
In total, these 4 companies had data breaches on over 400M customer records. For some including email, telephone numbers, customer IDs but also credit card numbers, birth dates and addresses. These 4 cases still count among the top 10 cyber incidents of all time.
Two days ago security researcher Chris Roberts claimed that he hacked a plane in mid-flight. Roberts allegedly accessed the planes’ network through the in-flight entertainment system. He also claims that this hack allowed him access to critical systems such as the fuel balancing and thrust control systems.
Mr Roberts has told the FBI that he had been accessing these systems around 15 times between 2011 and 2015.
One biggest threats in cyber security remains outdated software. Many of these in-flight entertainment systems are between 5 and 10 years old and can be hacked quite easily according to numerous researchers. Similar risks exist for businesses that are using outdated software, as the original vendors often stop fixing bugs and adding patches in favour of a more recent product.
At the time of writing, discussions are still ongoing on whether Roberts truly accessed certain avionic systems. Plane manufacturers claim that these are separated from in-flight entertainment systems and cannot be accessed from any passenger seat. This looks like it might be a hacking saga and was destined as a marketing coup for Roberts.
With the Internet of Things and cloud based computing making immense progress in business applications and consumer products, cyber security threats will increase as well.
Mapping The Network
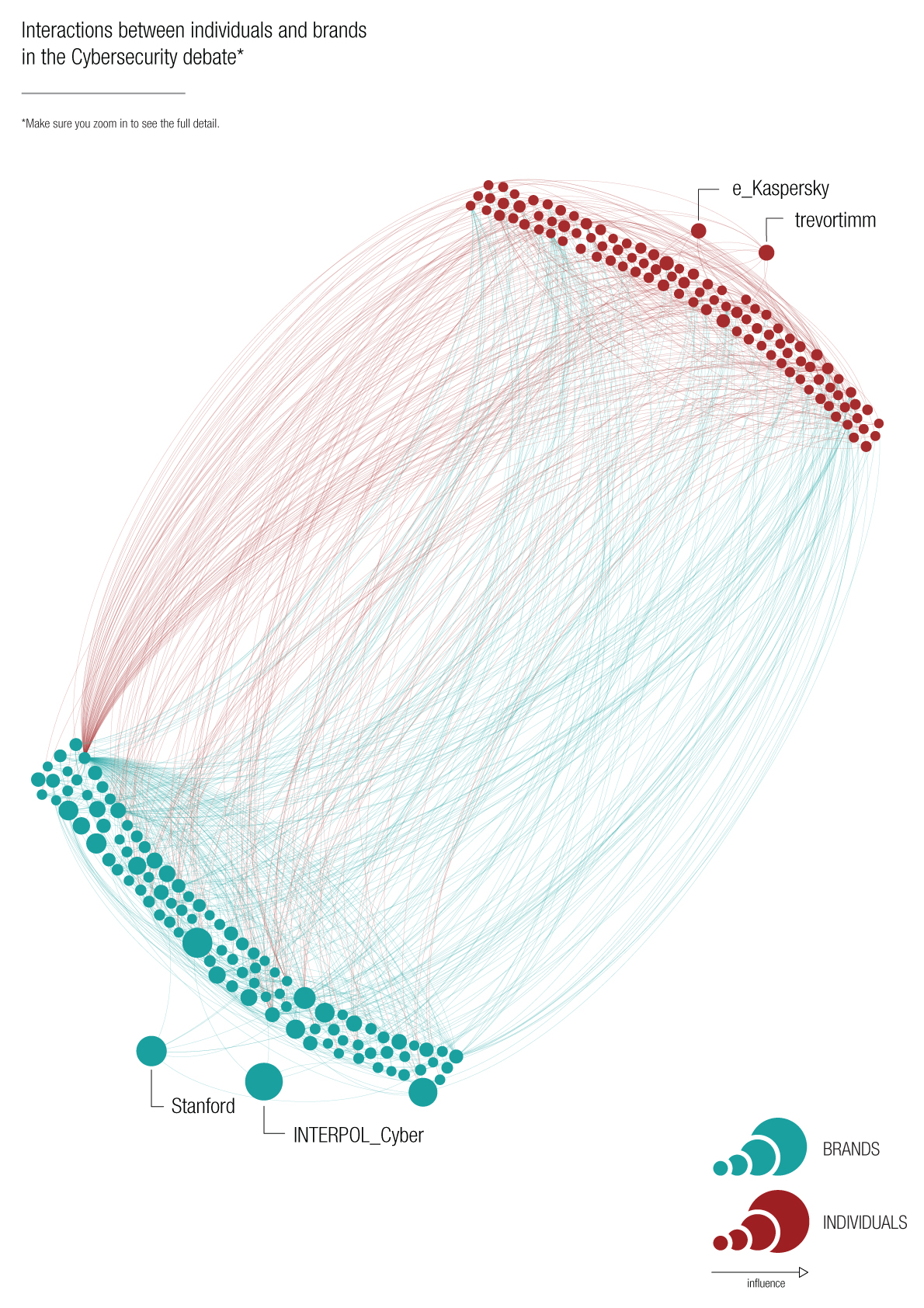
When analysing the network map (+160k users) on cybersecurity we can immediately see the difference in the size of nodes between the brands (in blue) and the individuals (in red). The brands are more influential in this particular discussion and seem to be driving the cybersecurity discussion more than the individuals.
These network maps are great way of understanding key discussions on social media between brands and individuals. Kasperksy and Interpol_Cyber are the most influential nodes, but the interactions are truly driven by the smaller brands. Illustrating this is Treadstone71LLC which is the node located upper left in the brands (blue) and counts an enormous amount of interactions towards the individuals (red lines) as well as the brands (blue lines). Keep scrolling to find out who ranks among the most influential in cybersecurity.
Top 100 Individuals
At Onalytica we knew that cybersecurity was a big topic in traditional media as well as social media. We analysed over 600,000 tweets over the past +90 days to present insightful data on who is truly leading this trending discussion. Stay up to date on what’s hot in cybersecurity by downloading our full report just below.

DOWNLOAD THE FULL REPORT
| Rank | Twitter Handle | Name | PageRank (Normalised) |
|---|---|---|---|
| 1 | @trevortimm | Trevor Timm | 100 |
| 2 | @e_kaspersky | Eugene Kaspersky | 90.94 |
| 3 | @gabeygoh | Gabey Goh | 77.1 |
| 4 | @BenDiPietro1 | Ben DiPietro | 65.01 |
| 5 | @GovInfoSecurity | Eric Chabrow | 47.56 |
| 6 | @zackwhittaker | Zack Whittaker | 43.12 |
| 7 | @ZDNetCharlie | Charlie Osborne | 39.33 |
| 8 | @granick | Jennifer Granick | 37.55 |
| 9 | @SaraSorcher | Sara Sorcher | 37.26 |
| 10 | @peterwsinger | Peter W. Singer | 36.19 |
| 11 | @ErrataRob | Rob Graham | 35.99 |
| 12 | @KevinBankston | Kevin Bankston | 35.23 |
| 13 | @froomkin | Dan Froomkin | 34.64 |
| 14 | @ron_miller | Ron Miller | 32.92 |
| 15 | @Beaker | Hoff | 32.67 |
| 16 | @Jose_Pagliery | Jose Pagliery | 30.75 |
| 17 | @garyjdavis | Gary Davis | 30.2 |
| 18 | @FutureCrimes | Marc Goodman | 29.15 |
| 19 | @benatworkdc | Ben FitzGerald | 28.95 |
| 20 | @SangerNYT | David Sanger | 28.51 |
| 21 | @attackerman | Spencer Ackerman | 27.98 |
| 22 | @kevinmitnick | Kevin Mitnick | 27.37 |
| 23 | @HurdOnTheHill | Rep. Will Hurd | 25.21 |
| 24 | @alex | Alex | 24.7 |
| 25 | @eliseviebeck | Elise Viebeck | 24.26 |
| 26 | @MikeDeCesare | Mike DeCesare | 24 |
| 27 | @adschina | Adam Segal | 23.84 |
| 28 | @LaMonicaBuzz | Paul R. La Monica | 23.69 |
| 29 | @emm_david | David Emm | 23.41 |
| 30 | @shaneharris | Shane Harris | 23.32 |
| 31 | @damianpaletta | Damian Paletta | 23.17 |
| 32 | @robertherjavec | Robert Herjavec | 22.83 |
| 33 | @taosecurity | Richard Bejtlich | 22.57 |
| 34 | @joltsik | Jon Oltsik | 21.51 |
| 35 | @Aliya_NextGov | Aliya Sternstein | 21.11 |
| 36 | @WeldPond | Chris Wysopal | 20.74 |
| 37 | @RAPst4r | Reuben Paul | 20.23 |
| 38 | @nealunger | Neal Ungerleider | 19.95 |
| 39 | @mikkosniemela | Mikko S. Niemelä | 19.48 |
| 40 | @kimberlyanngeo | Kimberly George | 18.88 |
| 41 | @RobertMLee | Robert M. Lee | 18.59 |
| 42 | @kmingis | Ken Mingis | 18.49 |
| 43 | @editingwhiz | Chris Preimesberger | 18.44 |
| 44 | @juliusclark | Julius | 17.68 |
| 45 | @ananalytical | Josh Goldfarb | 17.63 |
| 46 | @sfwriter | Rachael King | 17.62 |
| 47 | @ericgeller | Eric Geller | 17.26 |
| 48 | @johncvillanueva | John Carl Villanueva | 17.19 |
| 49 | @Bob_Moritz | Bob Moritz | 17.09 |
| 50 | @craigbrownphd | Craig Brown, Ph.D. | 16.93 |
Top 100 Brands
In our brands analysis it was not surprising finding the handles from Interpol and Homeland Security in the top 10, as cybersecurity is a big challenge for governments in the coming decades. The top 100 contains an expected mix of government, business and journalistic brands. Kaspersky, Symantec, IBM and Raytheon are among the top 50 including well-known publications like Computerworld, TechCrunch, CIO.com and many more.
Be sure to grab the full top 100 report to see where brands like Juniper Networks, Intel Security, RSA Security, Cisco Security, CA technologies, Veracode, Imperva and many more rank.

DOWNLOAD THE FULL REPORT
| Rank | Twitter Handle | Name | PageRank (Normalised) |
|---|---|---|---|
| 1 | @INTERPOL_Cyber | INTERPOL_Cyber | 100 |
| 2 | @Stanford | Stanford University | 74.67 |
| 3 | @TrendMicro | Trend Micro | 73.3 |
| 4 | @kaspersky | Kaspersky Lab | 69.09 |
| 5 | @RSAConference | RSA Conference | 44.97 |
| 6 | @Recode | Re/code | 39.35 |
| 7 | @ZDNet | ZDNet | 37.78 |
| 8 | @symantec | Symantec | 37.56 |
| 9 | @DHSgov | Homeland Security | 35.78 |
| 10 | @TechCrunch | TechCrunch | 31.73 |
| 11 | @SputnikInt | Sputnik | 29.21 |
| 12 | @FireEye | FireEye | 28.98 |
| 13 | @CyberExaminer | Digital Forensics | 27.62 |
| 14 | @CIOonline | CIO.com | 26.6 |
| 15 | @IBMSecurity | IBM Security | 26.1 |
| 16 | @Computerworld | Computerworld | 24.93 |
| 17 | @LogRhythm | LogRhythm | 24.5 |
| 18 | @NewAmerica | New America | 22.89 |
| 19 | @WIRED | WIRED | 22.79 |
| 20 | @DarkReading | DarkReading | 20.91 |
| 21 | @CSMPasscode | CSMPasscode | 20.37 |
| 22 | @VZEnterprise | Verizon Enterprise | 19.13 |
| 23 | @MEMMOSdubai | MEMMOS Enterprises | 19.01 |
| 24 | @EFF | EFF | 18.65 |
| 25 | @ReutersTech | Reuters Tech News | 18.51 |
| 26 | @nuix | Nuix | 18.43 |
| 27 | @DNewsAsia | Digital News Asia | 18.05 |
| 28 | @SCMagazine | SCMagazine | 17.67 |
| 29 | @cyber | Cybersecurity | 17.21 |
| 30 | @ISACANews | ISACA International | 16.53 |
| 31 | @InfosecurityMag | Infosecurity | 15.3 |
| 32 | @Slate | Slate | 13.73 |
| 33 | @Security_411 | Security_411 | 13.61 |
| 34 | @NSA_PAO | NSA/CSS | 13.39 |
| 35 | @NuHarbor | NuHarbor Security | 13.12 |
| 36 | @Raytheon | Raytheon | 12.77 |
| 37 | @ITworld | ITworld | 10.62 |
| 38 | @Treadstone71LLC | Treadstone 71 | 10.5 |
| 39 | @dhsscitech | DHS S&T | 10.26 |
| 40 | @FierceHealthIT | FierceHealthIT | 10.21 |
| 41 | @SecurityWeek | SecurityWeek | 10.06 |
| 42 | @Inc | Inc. | 10.01 |
| 43 | @ITBusinessEdge | IT Business Edge | 9.8 |
| 44 | @Techmeme | Techmeme | 9.77 |
| 45 | @Cyveillance | Cyveillance | 9.6 |
| 46 | @enisa_eu | ENISA | 9.56 |
| 47 | @mashable | Mashable | 9.39 |
| 48 | @CSOonline | CSOonline | 9.36 |
| 49 | @verge | The Verge | 9.28 |
| 50 | @VentureBeat | VentureBeat | 9.27 |
At Onalytica we love building these lists and want to give back to our loyal readers as much as we can. If you’re interested in other topics (such as Machine to Machine , Wearables , Internet of Things , …) be sure to have a gander on our blog or why not propose some topics to us on twitter? We also build some very cool software to manage all of these influencers. Get a free demo today by clicking the button below!
REQUEST A FREE DEMO
TAGS
CYBERSECURITY 2015:
TOP 100 INFLUENCERS AND BRANDS
Download this free report which reveals the top 100 cybersecurity influencers and brands