The data security market is estimated to be worth in excess of $202 Billion by 2021, growing at an annual rate of 9.8%. The number of seven-figure deals alone has grown by 40% year-on-year since 2010. With more data online now than ever before, the importance of securing and protecting your data from destructive forces and the unwanted actions of unauthorised users, has never been more important. Some common measures taken to secure data include scrambling, where data is rendered unreadable to unauthorised users and hackers, and locking computer systems with a password and installing a firewall system. Organisations can also consider imposing non-disclosure agreements for users of confidential data, and reminding them not sending personal or confidential data via email or other file transfer means without first encrypting them. As a last resort data can be destroyed when needed.
The data security field is also of growing importance due to the growth of smart devices, including smartphones, televisions as part of the Internet of Things. With these new technologies comes new risks and threats which have to be defended to protect sensitive information. Organisations are having to boost their security budgets and adopt new innovative technologies to respond the rising risks of cyber crime.
WHAT ARE THE INFLUENCERS SAYING?
We reached out to some of the top influencers on our list to ask them for their views on data security. We spoke to Fabienne Neymarck (#2), Dr. Carlo Piltz (#3), Bill Kleyman (#4), Giovanni Buttarelli (#7), Lisa Briercliffe (#8), Evan Kirstel (#11), Jonathan Armstrong (#14), Kirk Borne (#16) and Tripp Braden (#18). Be sure to follow them to stay up to date on the best content and resources on data security.
 Fabienne Neymarck – Sales Administration at Ascendeo France
Fabienne Neymarck – Sales Administration at Ascendeo France
“Cyber attacks are in fast expansion and getting increasingly sophisticated all over the world. Many companies do not have RSSI. There is an increase with new technologies (IoT), the smartphone accumulates a part of our activity on the Internet, stores our contacts, our SMS, our emails, in short, the smartphone has become a computer. Neither professionals, nor individuals are immune to online piracy. Digital and internet technologies are the backbone of our society. All the networks, current and future information systems, must be secured to preserve privacy and the proper operation of the online economy.”
 Dr. Carlo Piltz – Lawyer at JBB Law and Co-Editor of Privacy in Germany at PinG Journal
Dr. Carlo Piltz – Lawyer at JBB Law and Co-Editor of Privacy in Germany at PinG Journal
“Data Security and Data Privacy are already now important factors for the industry. On the one hand, companies are legally obliged to implement certain security standards and to process personal data only in accordance with certain principles. In this regard, Data Security and Data Privacy are a necessary compliance component. On the other hand, Data Security and Privacy play a key role in the creation of trust for digital services and for the fostering of new innovative products. This importance of Data Security and Data Privacy will especially increase in our digitized world. Data, may it be personal or not, will even more be considered as a valuable asset. The security of this asset as well as the adequate handling of the data in accordance with applicable laws will be one of the future challenges as well as chances for the industry.”
 Bill Kleyman – Vice President of Strategy and Innovation at MTM
Bill Kleyman – Vice President of Strategy and Innovation at MTM
“There was a great security study which pointed out that the rapid digitization of consumers’ lives and enterprise records will increase the cost of data breaches to $2.1 trillion globally by 2019. This is an increase of almost four times the estimated cost of breaches in 2015. Here’s the reality – attacks against critical data points will absolutely continue to grow and evolve. Why? Your data continues to become more important to the business – and a lot more valuable. As we examine the future IT and business landscape we see more interconnected devices, more users, more services being delivered, and – very importantly – we are experiencing the digital revolution. Organizations of all sizes across all verticals are using new digital tools to be productive and create competitive advantages. The digitization of our world helps create new kinds of opportunities; as well as new types of risks. Looking ahead, your security model must be end-to-end and incorporate all of your digital content and data points. Along the same lines, you need to remember one very important rule: When it comes to security, there is no silver bullet. Your traditional firewall architecture alone will not stop new kinds of advanced persistent threats (APTs) taking aim at services, applications, key systems, users, and your data. Organizations with IT locations on premise and in the cloud will have to adopt new kinds of security systems which support more data points, mobile users, and evolving business models. Bottom line: always look at the big security picture; and – learn to understand the real value of your data.”
 Giovanni Buttarelli – European Data Protection Supervisor
Giovanni Buttarelli – European Data Protection Supervisor
“Ensuring a high level of security for personal data, systems and networks is a legal requirement in Europe and in many other parts of the world. It is also recognised globally as furthering the interests of companies, organisations and public administration bodies, which rely on the use of information to carry out their daily business and attach great importance to the value and efficiency of their work. It is essential that these entities implement a new generation of modern measures, taking into account both the high standards required and the cost of implementation. The integrity of their systems is key for the rights, freedoms and legitimate interests of the individuals involved, as well as for the digital market. We encourage data controllers and processors to engage in the development of dynamic security measures, appropriate to the increasing risks, and to use information security risk management processes to address their specific needs, including cybercrime prevention. Legal and technical measures alone cannot solve the issue of information security. We count on data processing accountability, a new approach to data protection which is increasingly used around the world. An organisation’s hierarchy should ultimately be responsible for the implementation of information security solutions and the IT infrastructure that support them. High level management has to facilitate the development of robust policies and to mobilise the internal and external, financial and human resources required to counter the information and data risks that an organisation faces.”

Lisa Briercliffe – Principal Consultant at Briercliffe Associates
“Data security is widely misunderstood and in some cases it is even ignored. It has impacts at every level of society from the man in the street through all levels of business to government both local, central and beyond. Getting it right starts with understanding it. International standards are really quite important though they are too often ignored. Those who make products in information technology are responsible for building security into what they offer and there is a way to go. The real problem here is that none of us only use the products of one supplier and therefore whatever a given supplier does, there is a need at the systems level above that for comprehensive management. Even more important is the existence of daily and periodic methods and routines on the part of the person and company to ensure that the biggest risk, which is the people, is being appropriately mitigated. I would suggest that the issues of data security will never go away with threats being created and discovered on an almost daily basis. We all have to become more proficient and recognise the risks and then take the appropriate action to remain as safe as is possible.”
 Evan Kirstel – Social Media Business Strategist (Advisor) at UCStrategies.com
Evan Kirstel – Social Media Business Strategist (Advisor) at UCStrategies.com
“The Internet of Things will become a more ripe attack target and Ransomware will expand into into devices like cars, wearables and medical devices. Most wearables for example, lack basic security features or endpoint protection. This will introduce new threats such as collision among connected cars (a brand new potential scandal rivalling the Toyota acceleration stories of the 90s); stolen personal information about users’ smart home info; and attackers locking medical devices until a ransom is paid. Welcome to the Internet of (insecure) things!”
 Jonathan Armstrong – Partner at Cordery
Jonathan Armstrong – Partner at Cordery
“Information security continues to be one of the biggest boardroom challenges. Threats are increasing in sophistication with advanced financial scams, rogue employees and state sponsored attacks. The consequences are greater too with new regulation like GDPR & greater impact on share price. Doing nothing isn’t an option – companies need to shore up their defences and learn how to react to threats quickly.”
 Kirk Borne – Principal Data Scientist at Booz Allen Hamilton
Kirk Borne – Principal Data Scientist at Booz Allen Hamilton
“The tension between security and privacy has never been as pronounced as it is now, in the world of data. Knowing as much as you can about users and customers in order to provide essential security by discovering potential risk areas (such as insider threats, adversaries, and bad actors) is at odds with the desire to protect the privacy of each individual’s personal information. Strong data policies around data governance, stewardship, security, and privacy are obviously fundamental. Moving beyond policy and into practice, do your people know the important differences and occasional similarities between private, secure, confidential, personal, proprietary, and open data? They should! This understanding begins with a culture of data — placing data squarely in the purview of all organizational discussions, decisions, and operations. Building a culture of data starts at the top, and at the bottom, and in the middle — everyone in the organization needs data governance, security, and privacy awareness training. Do it today. Don’t wait!”
 Tripp Braden – Managing Partner at Strategic Performance Partners
Tripp Braden – Managing Partner at Strategic Performance Partners
“Data security continues to be a high priority for our organizations. We invest significant resources to protect our customers’ and partners’ data. The question we must continue to ask ourselves is: How can we increase impact and influence on our organization’s success? As with many technology challenges of the past, we may miss the bigger picture of how data security can be used for competitive advantage in our markets. The next generation of data security will not only continue to protect our data, but provide insights as to what might be happening in our markets. It will enable our business strategy and success. Sharing this critical information allows data security leaders to provide actionable insights for our organizations to create higher levels of trust and collaboration with customers, partners, and clients. This means additional resources and funding allocated to data security. We can move from a corporate expense to a source of unique differentiation in our global markets. Understanding the many possibilities of data security should enable us to build more sustainable organizations and careers. Are we ready to take on this challenge?”
TOPIC ANALYSIS
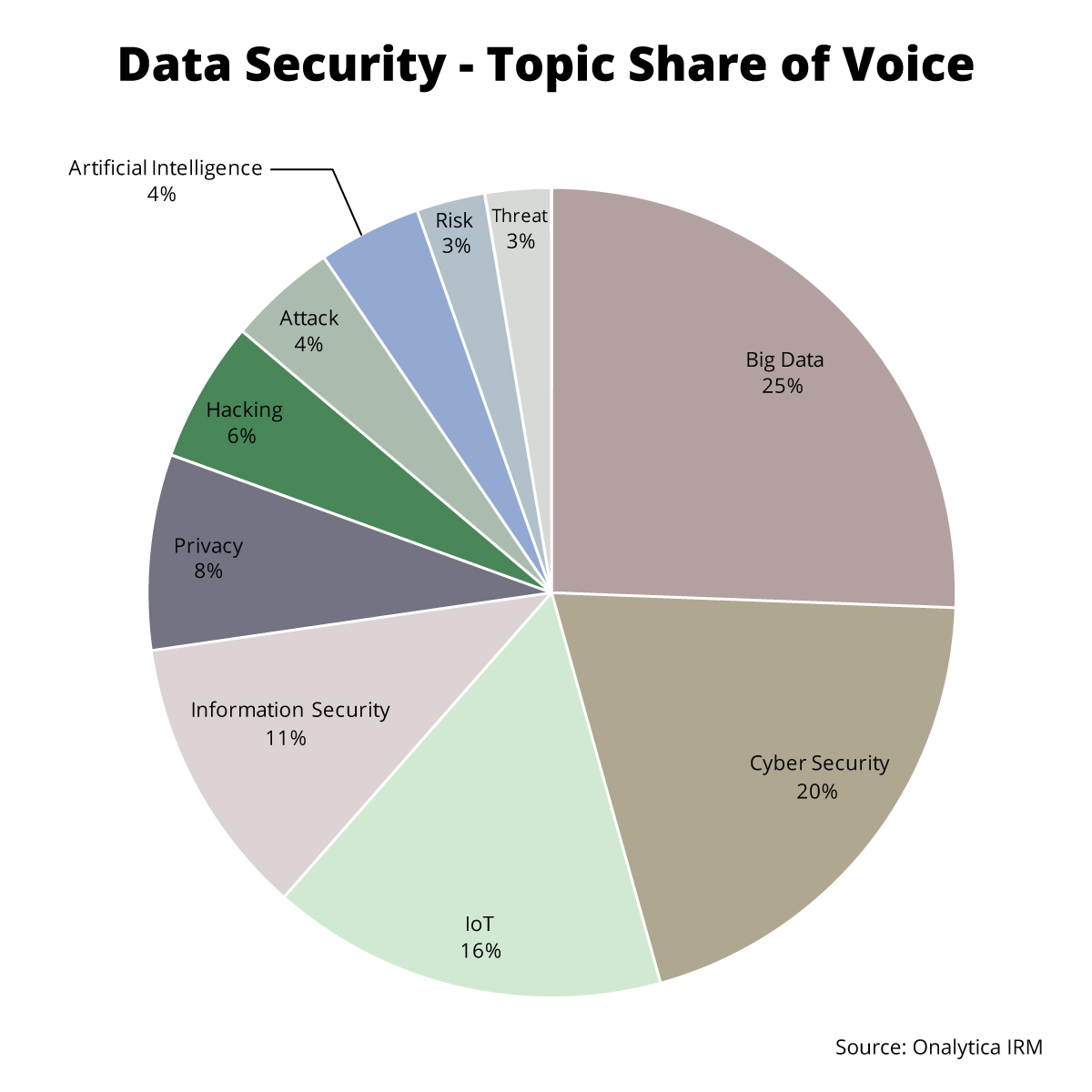
We were interested in seeing which topics were most popular among the top data security influencers, so we analysed their tweets and blogs from 1st January – 9th August 2016 and counted mentions of various topics associated with data security, which we then used to create a topic share of voice chart.
It’s interesting to note that the most popular topic among the data security influencers was Big Data with a 25% share of voice, illustrating the fact that big data and its use within the data security sector is a key debate driver among the top influencers. Cyber Security was the 2nd most popular debate driver with 20%, followed by mentions of IoT with a 16% share of voice, illustrating the level of perceived threats within the IoT sector. Information Security received an 11% share of voice followed by Privacy with 8%. Other frequently mentioned topics among the top influencers included Hacking, Attack, Artificial Intelligence, Risk and Threat.
MAPPING THE DATA SECURITY COMMUNITY
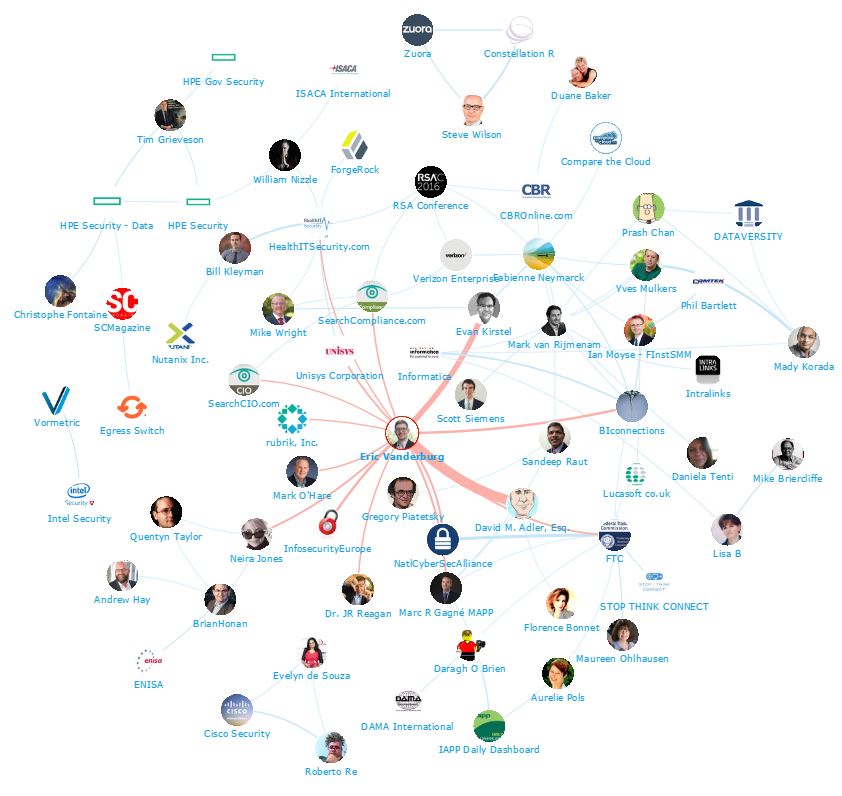
We were very interested in seeing which Data Security influencers and brands were leading the online discussion, so we analysed tweets over the last 6 months mentioning the keywords: “data privacy” OR dataprivacy OR “data security” OR datasecurity OR datasec OR “data protection” OR dataprotection. We then identified the top 100 most influential brands and individuals leading the discussion on Twitter. What we discovered was a very engaged community, with much discussion between individuals and brands. Below you can see a network map of the online conversation with the influencer Eric Vanderburg at the centre. This map was created with our Influencer Relationship Management software (IRM). Be sure to click on the map to enjoy the full size network diagram in greater detail.
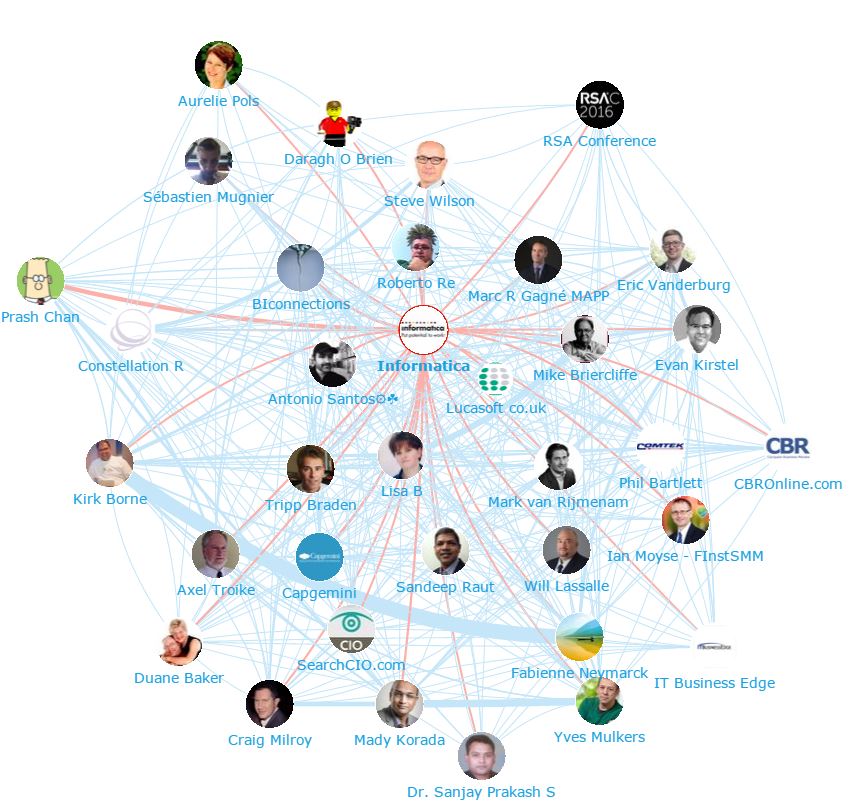
Below you can see another network map created with our Influencer Relationship Management software (IRM) showing the number 1 brand Informatica at the centre and all the conversations to and from the influencers in their field. If you are interested in learning more about identifying, managing and engaging with influencers click here to get in touch!
TOP 100 INDIVIDUALS
We looked at all the individuals engaging on Twitter to bring you a list of the top influencers in Data Security. Below is the top 50, if you want to see who ranks from 50-100 be sure to download the full report by clicking the download button below.

DOWNLOAD THE FULL REPORT
| Rank | Twitter Handle | Name | Company | Influencer Score |
|---|---|---|---|---|
| 1 | @JanAlbrecht | Jan Philipp Albrecht | European Parliament | 100 |
| 2 | @ArkangelScrap | Fabienne Neymarck | Ascendeo | 85.38 |
| 3 | @CarloPiltz | Dr. Carlo Piltz | JBB Rechtsanwaelte | 84.13 |
| 4 | @QuadStack | Bill Kleyman | MTM Technologies | 73.19 |
| 5 | @MOhlhausenFTC | Maureen Ohlhausen | Federal Trade Comission | 71.86 |
| 6 | @roomeezon | Imran Hafeez Panhwar | Government of Pakistan | 60.38 |
| 7 | @Buttarelli_G | Giovanni Buttarelli | European Parliament | 53.85 |
| 8 | @lisabriercliffe | Lisa B | Briercliffe Associates | 53.81 |
| 9 | @PaulNemitz | Paul Nemitz | European Comission | 51.78 |
| 10 | @ClaudeMoraesMEP | Claude Moraes MEP | European Parliament | 50.8 |
| 11 | @evankirstel | Evan Kirstel | UCStrategies.com | 48.72 |
| 12 | @evanderburg | Eric Vanderburg | JurInnov Ltd. | 48.16 |
| 13 | @AlexHorovitz | Alex Horovitz | Symantec | 44.4 |
| 14 | @armstrongjp | Jonathan Armstrong | Cordery | 40.03 |
| 15 | @amit_walia | Amit Walia | Informatica | 39.54 |
| 16 | @KirkDBorne | Kirk Borne | Booz Allen Hamilton | 39.02 |
| 17 | @kingofpayments | Christopher Danvers | AAFCU | 36.3 |
| 18 | @TrippBraden | Tripp Braden | Strategic Performance Partners | 34.76 |
| 19 | @mikejulietbravo | Mike Briercliffe | Briercliffe Associates | 34.48 |
| 20 | @neirajones | Neira Jones | Global Cyber Alliance | 34.29 |
| 21 | @kdnuggets | Gregory Piatetsky | Kdnuggets | 33.06 |
| 22 | @RobRe62 | Roberto Re | HRD Training Group | 32.88 |
| 23 | @akwyz | Antonio Santos | Atos UK & IE | 27.64 |
| 24 | @daraghobrien | Daragh O Brien | Law Society of Ireland | 26.53 |
| 25 | @Jbuff | Jason Buffington | Enterprise Strategy Group | 26.36 |
| 26 | @thomascmurray | Tom Murray | Alliance for Excellent Education | 25.86 |
| 27 | @vishne0 | Vishal Sharma | Security-india | 25.61 |
| 28 | @AverageJoeVC | Manolis Sfinarolakis | Reality Crowd TV Media Corporation | 25.45 |
| 29 | @CraigMilroy | Craig Milroy | Sun Life Financial | 25.01 |
| 30 | @DrSanjayPSahoo | Dr. Sanjay Prakash S | Ssfglobal.com | 24.39 |
| 31 | @MWiFRC | Mike Wright | MWi Forensic Risk Consulting | 24.08 |
| 32 | @AureliePols | Aurelie Pols | IE Business School | 23.93 |
| 33 | @glynmoody | Glyn Moody | opendotdot | 22.83 |
| 34 | @YvesMulkers | Yves Mulkers | GSK | 22.74 |
| 35 | @SimonCocking | Simon Cocking | Irish Tech News | 22.42 |
| 36 | @BrianHonan | BrianHonan | BH Consulting | 22.1 |
| 37 | @LenniMontiel | Lenni Montiel UNDESA | United Nations | 21.94 |
| 38 | @bill_nizzle | William Nizzle | ICIT | 21.8 |
| 39 | @vGazza | Rodrigo Gazzaneo | EMC | 19.91 |
| 40 | @DBaker007 | Duane Baker | dba Duane Baker | 19.79 |
| 41 | @gmt71_01 | Gianmarco Troia | Det Norske Veritas | 19.54 |
| 42 | @cjiqbal | Chaudhry Javed Iqbal | British Council | 19.37 |
| 43 | @guychurchward | Guy Churchward | EMC | 18.65 |
| 44 | @e_desouza | Evelyn de Souza | Cisco | 18.5 |
| 45 | @smugnier | Sébastien Mugnier | No Web Agency | 18.29 |
| 46 | @Phil_Comtek | Phil Bartlett | Comtek | 17.85 |
| 47 | @scottdelandy | scott delandy | EMC | 16.83 |
| 48 | @imoyse | Ian Moyse | Axios Systems | 15.53 |
| 49 | @peterku | Peter Ku | Informatica | 15.25 |
| 50 | @OttLegalRebels | Marc R Gagné MAPP | PACC | 15.2 |
TOP 100 BRANDS
We also looked at all the brands engaging on Twitter to bring you a list of the top data security brands. Below is the top 50, if you want to see who ranks from 50-100 be sure to download the report to get the full top 100 list, and see who are most the influential brands in data security.

DOWNLOAD THE FULL REPORT
| Rank | Twitter Handle | Name | Influencer Score |
|---|---|---|---|
| 1 | @Informatica | Informatica | 100 |
| 2 | @EU_EDPS | EDPS | 95.23 |
| 3 | @FTC | FTC | 84.75 |
| 4 | @EMCProtectData | EMC Data Protection | 70.79 |
| 5 | @CiscoSecurity | Cisco Security | 55.4 |
| 6 | @hpe_voltage | HPE Security – Data | 52.38 |
| 7 | @SecurityHIT | HealthITSecurity.com | 50.02 |
| 8 | @biconnections | BIconnections | 47.65 |
| 9 | @Treadstone71LLC | Treadstone 71 | 42.7 |
| 10 | @SCMagazine | SCMagazine | 36.35 |
| 11 | @ValencyNetworks | Valency Networks | 30.2 |
| 12 | @AtlanticCouncil | AtlanticCouncil | 29.4 |
| 13 | @Insafenetwork | Insafe | 27.33 |
| 14 | @Capgemini | Capgemini | 26.01 |
| 15 | @SecurityWeek | SecurityWeek | 25.64 |
| 16 | @DZone | DZone | 21.45 |
| 17 | @HPE_GovSec | HPE Gov Security | 21.01 |
| 18 | @FSecure | F-Secure | 20.6 |
| 19 | @Europol | Europol | 20.54 |
| 20 | @Galaxkey | Galaxkey | 20.5 |
| 21 | @Vormetric | Vormetric | 19.99 |
| 22 | @UK_SIC | UK Safer Internet | 18.95 |
| 23 | @DailyDashboard | IAPP Daily Dashboard | 18.01 |
| 24 | @ITBusinessEdge | IT Business Edge | 17.55 |
| 25 | @HPE_Security | HPE Security | 17.55 |
| 26 | @PrivacyCamp | Privacy Camp | 17.5 |
| 27 | @Fortinet | Fortinet | 17.1 |
| 28 | @SimpliVityCorp | SimpliVity | 16.8 |
| 29 | @futureofprivacy | Future of Privacy | 16.33 |
| 30 | @Forcepointsec | Forcepoint LLC | 15.96 |
| 31 | @INTERPOL_HQ | INTERPOL | 15.86 |
| 32 | @nutanix | Nutanix Inc. | 15.84 |
| 33 | @DellDP | Dell Data Protection | 15.81 |
| 34 | @cbronline | CBROnline.com | 15.38 |
| 35 | @RSAConference | RSA Conference | 15.29 |
| 36 | @ITGovernance | IT Governance | 14.91 |
| 37 | @AccentureTech | Accenture Technology | 14.8 |
| 38 | @unisyscorp | Unisys Corporation | 14.67 |
| 39 | @HPE_Software | HPE Software | 14.35 |
| 40 | @Intralinks | Intralinks | 14.21 |
| 41 | @PwCAdvisory | PwC Advisory | 13.65 |
| 42 | @UnisconGmbH | Uniscon GmbH | 13.3 |
| 43 | @delphix | Delphix | 13.25 |
| 44 | @IDGCN | Technology Experts | 13.12 |
| 45 | @DellSecurity | Dell Security | 12.75 |
| 46 | @Dataversity | DATAVERSITY | 12.7 |
| 47 | @AscotBarclay | Ascot Barclay Cyber | 12.69 |
| 48 | @StaySafeOnline | NatlCyberSecAlliance | 12.65 |
| 49 | @Doorda | Doorda | 12.58 |
| 50 | @ForgeRock | ForgeRock | 12.44 |
At Onalytica we love building these lists and want to give back to our loyal readers as much as we can. If you’re interested in other topics (such as Virtual Reality, Digital Health, Digital Marketing) be sure to have a gander on our blog or why not propose some topics to us on twitter? We also build some very cool software to manage all of these influencers. Get a free demo today by clicking the button below!
Disclaimer: As ever with these lists, it must be stressed that the ranking is by no means a definitive measurement of influence, as there is no such thing. The brands and individuals listed are undoubtedly influential when it comes to driving discussion around Data Security.
The PageRank based methodology we use to extract influencers on a particular topic takes into account the number and quality of contextual references that a user receives. These calculations also take into account a user’s relevance (number of tweets on topic) and reach (number of followers). If you want to learn more, please read our article that outlines influencer identification.
TAGS
DATA SECURITY:
TOP 100 INFLUENCERS AND BRANDS
Download this free report which reveals the top 100 Data Security influencers and brands