Cyber Security and InfoSec remain critical concerns for brands and governments who need to safeguard their information against espionage attacks and criminal or negligent behaviour. Data breaches are becoming all too common, the recent leak from the Panamanian law firm Mossack Fonseca is one of the world’s largest data leaks to date (Over 11.5 Million Leaked Files including 2.6 Terabytes of Data) exposing an enormous web of offshore companies used to evade tax.
Any brand or agency who has a database of emails, telephone numbers, customer IDs, credit card numbers, birth dates, addresses and other sensitive information has a need to protect themselves from hackers. According to the latest annual TechTarget/Computer Weekly IT Spending Priorities survey, Data loss prevention (DLP) is going to be the top security initiative by UK firms in 2016. This demand has led to a wealth of experts who can help your brand test your information security, ascertain vulnerabilities and make recommendations to mitigate risks.
WHAT ARE THE EXPERTS SAYING?
We reached out to some of the top 20 influencers to ask them for their views on Cyber Security and InfoSec. We spoke to Daniel Miessler (#1), Khalil Sehnaoui (#2), Joseph Steinberg (#3), Lesley Carhart (#4), Ben Rothke (#14), Graham Penrose (#16) and Javvad Malik (#17). Be sure to follow them to stay up to date on the best content and resources on Cyber Security and InfoSec!
Daniel Miessler – Director of Client Advisory Services at IOActive
“The problem with most infosec programs is that they’re trying to add APT and threat intelligence components while nobody can produce a list of assets or describe their egress traffic. Corporate infosec suffers badly from jump, run, walk syndrome.”
 Khalil Sehnaoui – Founder & Managing Partner at Krypton Security
Khalil Sehnaoui – Founder & Managing Partner at Krypton Security
“Information Security is one of the main challenges of the 21st Century; albeit more intensely for wealthy and developed countries, when it comes to privacy, safety of personal and professional data and infrastructure integrity. The IoT (Internet of Things) phenomenon is filling our homes and workplaces with inter-connected devices that lack proper security hardening. This is due to the ever-rising demand for more facility, coupled with manufacturers’ desire to stay competitive. This competitive landscape has led some manufacturers to cut corners before launching products, because adequate security testing is viewed as too lengthy and costly of an investment. Moreover, governments have yet to put in place suitable pre-deployment standards, and to top it all off – country based legislations ache to follow global production and distribution channels. We must double our efforts in raising awareness as well as finding and implementing appropriate solutions to meet this challenge head-on and ensure our privacy and security on, and off, the Internet.”
Joseph Steinberg – Founder and CEO of Secure My Social
“As technology continues to increasingly permeate every aspect of our lives, information security has evolved from an esoteric concept into the greatest area of risk for many individuals, businesses, and even nations. Rapidly changing technologies and attack methods cause approaches and security countermeasures to quickly become outdated and ineffective; in order to stay safe, people and organizations must both remain constantly vigilant as well as leverage the wisdom of experts. Furthermore, changes in the ways that humans interact and communicate with one another have created extraordinary opportunities for criminals and other hackers; in order to succeed at delivering adequate protection, information security plans and the technologies utilized to implement them must incorporate mechanisms to addresses human weaknesses.”
 Lesley Carhart – Security Incident Response Lead at Motorola Solutions
Lesley Carhart – Security Incident Response Lead at Motorola Solutions
“The only way to shake the pervasive negative stereotypes which surround our infosec community is to represent ourselves positively to those outside it. We have a responsibility to inclusively guide those who have an interest in the field and seek our help. I’ve attempted to focus my efforts on making the information security field accessible and interesting to all – security impacts everyone and everyone has the potential to impact security.”
 Ben Rothke – Senior eGRC Consultant with Nettitude
Ben Rothke – Senior eGRC Consultant with Nettitude
“Perhaps one of the most devastating targeted attacks of recent months has been the attacks against medical centers in the United States. Just this week, the MedStar Health healthcare organization had to take a number of their systems offline. Critical systems went down such that patients could not book appointments and physicians could not look up messages or medical records. It’s not clear as of yet if this was a ransomware attack, in which a number of hospitals had to pay a ransom to recover their own data. But the message is clear, healthcare organizations are under attack. Hopefully they have a competent CISO to help them manage.”
 Graham Penrose – Blogger at Unamused Observer; AirGap Anonymity Collective; Anonymous Chronic
Graham Penrose – Blogger at Unamused Observer; AirGap Anonymity Collective; Anonymous Chronic
“Advocates and lobbyists for the maintenance of the right to privacy of ordinary citizens, their data and their digital communications are faced with powerful counter arguments. Arguments put forth by entities that seek to undermine these basic democratic rights in favour – they allege – of the “common good”. The justification of the erosion or indeed removal of these hard won freedoms is being proposed – it is argued – in favour of the more pressing imperative of national and trans-national security in light of global terror and cyber warfare threats. The historical requirements on law enforcement agencies in terms of the methods associated with the acquisition and preservation of evidence are being diluted and even bypassed in the cyber security context. “Forced Decryption Laws” are being considered in many jurisdictions and where they fail to grant access to the data being sought then subsequent refusal to provide that access by an activist or advocate or whistleblower or accused is being seen as an admission of guilt (inferences). This despite long respected laws providing protections associated with self-incrimination and the right to silence. The development of more sophisticated and intrusive technologies and powers, in certain cases, for use by law enforcement to counter national security threats is not the only pressing issue. The most important backdrop to this entire debate is not to forget what we are trying to protect in the first instance – democracy, privacy, the rights of the individual, free speech and the preservation of civil liberties.”
 Javvad Malik – Security Advocate at AlienVault
Javvad Malik – Security Advocate at AlienVault
“The Cyber security industry has grown at a rapid pace and plays an ever-increasing role in the world as we know it. Influencing the daily lives of individuals, or how how businesses and governments operate. As dependencies on technology increase as well as becoming more prevalent in everyday life with the internet of things, it is important Cyber Security figures out how to secure businesses, technologies and the underlying processes without getting in the way.”
MAPPING THE COMMUNITY
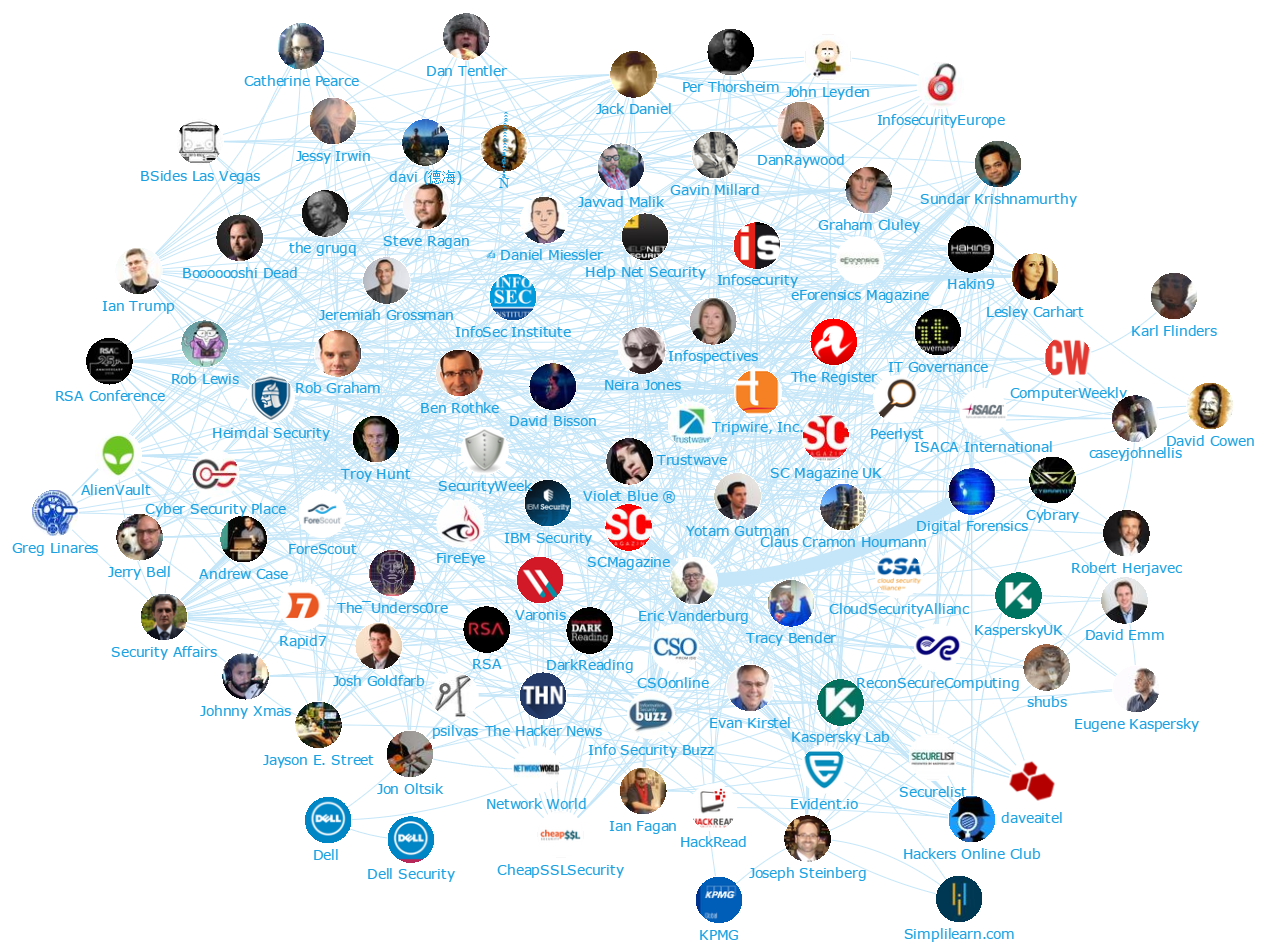
We were very interested in seeing which Cyber Security and InfoSec professionals and brands were leading the online discussion, so we analysed 817K+ tweets from November 30th 2015 to January 24th 2016 mentioning the keywords “Cyber Security” OR CyberSecurity OR Infosec OR “Information Security”. We then identified the top 100 most influential brands and individuals leading the discussion on Twitter. What we discovered was a very engaged community, with much discussion between individuals and brands. Below you can see a network map of the online conversation created with our Influencer Relationship Management software (IRM). Be sure to click on the map to enjoy the full size network diagram in greater detail.
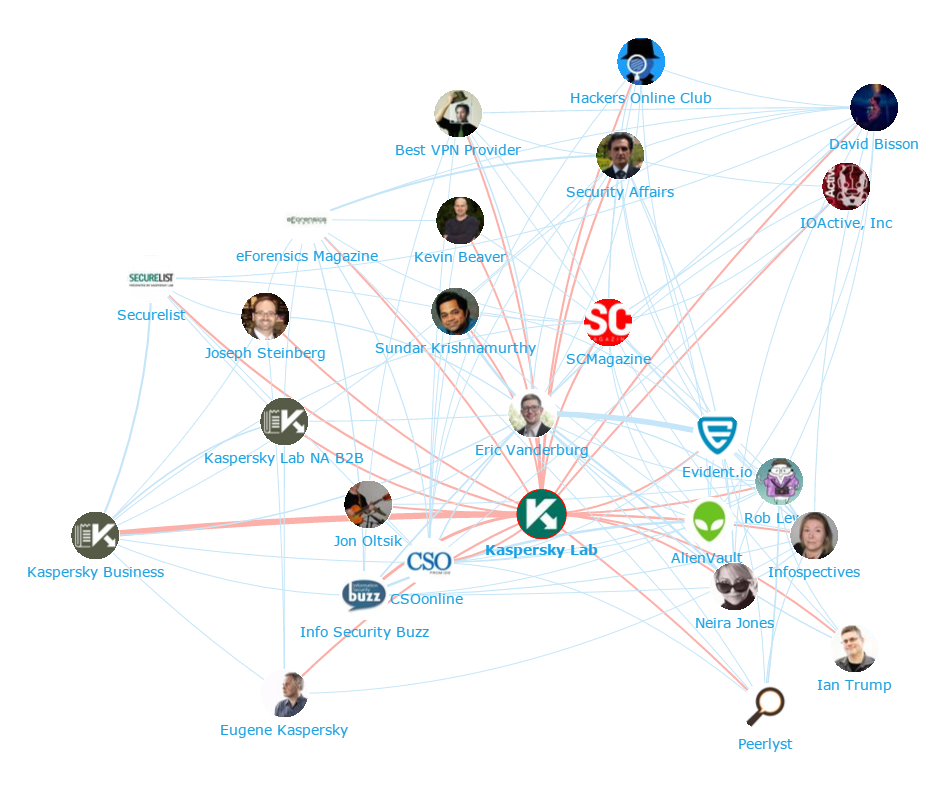
Below you can see another network map created with our Influencer Relationship Management software (IRM) showing the number 1 brand Kaspersky Lab at the centre, and the conversations to and from the different influencers in its field. If you are interested in learning more about identifying, managing and engaging with influencers click here to get in touch!
Top 100 INDIVIDUALS
We looked at all the individuals engaging on Twitter to bring you a list of the top 100 most influential individuals in the Cyber Security and InfoSec industry. Be sure to hit the download now button below to download the full report.

DOWNLOAD THE FULL REPORT
| Rank | Twitter Handle | Name | Company | Influencer Score |
|---|---|---|---|---|
| 1 | @DanielMiessler | Daniel Miessler | IOActive | 64.1 |
| 2 | @sehnaoui | Khalil (pilgrim) | Krypton Security | 43.85 |
| 3 | @JosephSteinberg | Joseph Steinberg | Secure My Social | 39.54 |
| 4 | @hacks4pancakes | Lesley Carhart | Motorola Solutions | 37.48 |
| 5 | @Laughing_Mantis | Greg Linares | Vectra | 34.09 |
| 6 | @thegrugq | the grugq | Independent Researcher, | 32.5 |
| 7 | @gmillard | Gavin Millard | Tenable Network Security | 30.63 |
| 8 | @jeremiahg | Jeremiah Grossman | WhiteHat Security | 25.59 |
| 9 | @chriseng | Chris Eng | Veracode | 24.1 |
| 10 | @Jhaddix | Jason Haddix | bugcrowd | 23.03 |
| 11 | @neirajones | Neira Jones | Independent Advisor | 22.83 |
| 12 | @mathewjschwartz | Mathew Schwartz | Information Security Media Group | 22.67 |
| 13 | @Cyb3rOps | Florian Roth | BSK Consulting | 21.53 |
| 14 | @benrothke | Ben Rothke | Nettitude | 21.12 |
| 15 | @todb | Tod Beardsley | Rapid7 | 20.77 |
| 16 | @GrahamPenrose2 | Graham Penrose | TMG Corporate Services | 20.33 |
| 17 | @J4vv4D | Javvad Malik | AlienVault | 17.06 |
| 18 | @evanderburg | Eric Vanderburg | Security Thinking Cap | 16.99 |
| 19 | @DilTown | Dillon | Trustwave | 16.7 |
| 20 | @DMBisson | David Bisson | Tripwire | 16.33 |
| 21 | @veorq | JP Aumasson | Kudelski Security | 15.48 |
| 22 | @infosec_au | shubs | Bishop Fox | 14.66 |
| 23 | @geminiimatt | matthew mitchell | Independent Researcher | 14.48 |
| 24 | @0xkitty | Christina Camilleri | Bishop Fox | 13.99 |
| 25 | @attrc | Andrew Case | Volexity | 13.98 |
| 26 | @matthew_d_green | Matthew Green | Johns Hopkins University | 13.91 |
| 27 | @KSZ714 | KSZ | Independent Consultant | 13.3 |
| 28 | @jleyden | John Leyden | The Register | 13.1 |
| 29 | @Infosec_Tourist | Rob Lewis | Trustifier | 12.61 |
| 30 | @0xUID | Anis Muslic | Freelance Security Analyst | 12.29 |
| 31 | @jesperjurcenoks | Jesper Jurcenoks | Alert Logic | 12.28 |
| 32 | @da_667 | DA_667 | Cisco | 12.01 |
| 33 | @deeks | Dennis Fratric | Independent Consultant | 11.99 |
| 34 | @Shirastweet | Shira Rubinoff | Secure My Social | 11.94 |
| 35 | @Karlfl | Karl Flinders | Computer Weekly | 11.84 |
| 36 | @juliusclark | Julius | Bank of America | 11.83 |
| 37 | @Kym_Possible | KymPossible | bugcrowd | 11.82 |
| 38 | @daviottenheimer | davi (德海) | flyingpenguin | 11.78 |
| 39 | @staatsgeheim | Maarten Boone | Fox-IT | 11.5 |
| 40 | @Viss | Dan Tentler | Phobos Group | 11.41 |
| 41 | @liamosaur | Liam | Consultant | 11.22 |
| 42 | @secvalve | Catherine Pearce | Cisco | 11.07 |
| 43 | @Scott_Helme | Scott | Pentest | 10.92 |
| 44 | @emm_david | David Emm | Kaspersky Lab | 10.02 |
| 45 | @kmburnham | Kristin Burnham | Independent Journalist | 9.94 |
| 46 | @MalwareJake | Jake Williams | Rendition Infosec | 9.7 |
| 47 | @J0hnnyXm4s | Johnny Xmas | RedLegg International | 9.69 |
| 48 | @CaseyFahey | Casey Fahey | NetGoalie | 9.66 |
| 49 | @harbend | Tracy Bender | The Security Awareness Company | 9.53 |
| 50 | @daveaitel | daveaitel | Immunity | 9.01 |
TOP 100 BRANDS
In the top 100 brands we can find a great selection of agencies, resources as well as industry heavyweights in Cyber Security and InfoSec. Be sure to hit the download now button below to download the full report.

DOWNLOAD THE FULL REPORT
| Rank | Twitter Handle | Name | Influencer Score |
|---|---|---|---|
| 1 | @kaspersky | Kaspersky Lab | 100 |
| 2 | @CyberExaminer | Digital Forensics | 60.67 |
| 3 | @TripwireInc | Tripwire, Inc. | 59.28 |
| 4 | @Bitdefender | Bitdefender | 57.57 |
| 5 | @nixcraft | nixCraft | 55.14 |
| 6 | @alertlogic | Alert Logic | 41.94 |
| 7 | @CSOonline | CSOonline | 39.29 |
| 8 | @FireEye | FireEye | 38.42 |
| 9 | @DarkReading | DarkReading | 35.35 |
| 10 | @InfosecurityMag | Infosecurity | 33.01 |
| 11 | @TheRegister | The Register | 30.67 |
| 12 | @IBMSecurity | IBM Security | 29.59 |
| 13 | @ComputerWeekly | ComputerWeekly | 27.78 |
| 14 | @TheHackersNews | The Hacker News | 27.27 |
| 15 | @torproject | torproject | 25.55 |
| 16 | @KasperskyLabB2B | Kaspersky Business | 23.48 |
| 17 | @SANSInstitute | SANS Institute | 23.45 |
| 18 | @SCMagazine | SCMagazine | 22.6 |
| 19 | @RSAConference | RSA Conference | 21.43 |
| 20 | @Info_Sec_Buzz | Info Security Buzz | 20.16 |
| 21 | @teamcymru | Team Cymru | 19.98 |
| 22 | @InfoSec_BT | TEISS | 19.81 |
| 23 | @sucurisecurity | Sucuri | 19.67 |
| 24 | @InformaticaCorp | Informatica Corp. | 19.57 |
| 25 | @IT_securitynews | IT Security News | 19.56 |
| 26 | @CyberDomain | CyberWarrior | 18.65 |
| 27 | @Dell | Dell | 18.5 |
| 28 | @IOActive | IOActive, Inc | 18.41 |
| 29 | @CIOonline | CIO.com | 18.11 |
| 30 | @SoldierUK | SoldierUK | 17.95 |
| 31 | @DellSecurity | Dell Security | 17.8 |
| 32 | @ISACANews | ISACA International | 17.23 |
| 33 | @CircleCityCon | Circle City Con | 16.74 |
| 34 | @Proofpoint | Proofpoint | 16.69 |
| 35 | @NorseCorp | Norse | 16.68 |
| 36 | @KPMG | KPMG | 16.66 |
| 37 | @CyberHitchhiker | Cx2H | 16.61 |
| 38 | @ptracesecurity | Ptrace Security GmbH | 16.6 |
| 39 | @cybraryIT | Cybrary | 15.94 |
| 40 | @enisa_eu | ENISA | 15.3 |
| 41 | @bestvpns | Best VPN Provider | 14.8 |
| 42 | @SCmagazineUK | SC Magazine UK | 14.77 |
| 43 | @SANSNetWars | SANS NetWars | 14.53 |
| 44 | @HOCupdate | Hackers Online Club | 14.52 |
| 45 | @volatility | volatility | 14.32 |
| 46 | @HeimdalSecurity | Heimdal Security | 13.54 |
| 47 | @shodanhq | Shodan | 13.33 |
| 48 | @info_CCI | CCI | 13.13 |
| 49 | @Peerlyst | Peerlyst | 12.75 |
| 50 | @SecurityWeek | SecurityWeek | 12.24 |
At Onalytica we love building these lists and want to give back to our loyal readers as much as we can. If you’re interested in other topics (such as Machine to Machine, Wearable Tech, Internet of Things) be sure to have a gander on our blog or why not propose some topics to us on twitter? We also build some very cool software to manage all of these influencers. Get a free demo today by clicking the button below!
Disclaimer: As ever with these lists, it must be stressed that the ranking is by no means a definitive measurement of influence, as there is no such thing. The brands and individuals listed are undoubtedly influential when it comes to driving discussion in the Cyber Security and InfoSec debate.
The PageRank based methodology we use to extract influencers on a particular topic takes into account the number and quality of contextual references that a user receives. These calculations are independent of a user’s number of followers, but we do filter our lists based on how much a user is engaged in the conversation and the influence they drive through their networks.
TAGS
CYBER SECURITY AND INFOSEC:
TOP 100 INFLUENCERS AND BRANDS
Download this free report which reveals the top 100 cyber security and infoSec influencers and brands